Integrating Oracle Integration Cloud (OIC) with Oracle Fusion Applications (Oracle EPM Cloud) using OAuth 2.0 can present challenges especially when your Fusion App is not federated with your OIC’s IDCS. In this post, I’ll walk you through a real-world scenario and architectural pattern for securing access using OAuth 2.0 in such environments.
First, your need to understand some concepts :
Standard Oracle SaaS Architecture:
Oracle provisions Fusion Applications like EPM, ERP, HCM, etc. with their own dedicated IDCS (or IAM domain). This is Oracle-managed and isolated from your Oracle PaaS services like OIC.
So in most cases:
- OIC has its own customer-managed IDCS (you control users, clients, federation, etc.)
- EPM/ERP has its own Oracle-managed IDCS (you register apps there, but don’t manage users/federation deeply)
This separation exists for security, lifecycle independence, and tenant isolation reasons.
Why this matters for OAuth integration?
When integrating OIC with EPM, to call EPM REST APIs for example:
- You register an OAuth client in the EPM IDCS (Oracle-managed).
- You configure the OAuth 2.0 connection in OIC, pointing to the /token endpoint of the EPM IDCS.
- You must either:
- Use a local FA(fusion app) user , if OIC and EPM are in the same IDCS.
- Or grant OIC app access , if they are in different IDCS.
What that means « Federation’ ?
Federation allows two identity systems to trust each other, so users or applications authenticated in one system can access resources in another without needing separate accounts.
In Oracle Cloud, federation typically means:
- The OIC tenant’s IDCS trusts the Fusion App’s IDCS (or vice versa).
- Users or clients from one IDCS can get tokens that are valid in the other system.
- FA and OIC in Same vs Different IDCS Tenants
OAuth authorization flow – When Fusion apps are not federated with IDCS
1. Define Trust Between IDCS and Fusion Apps
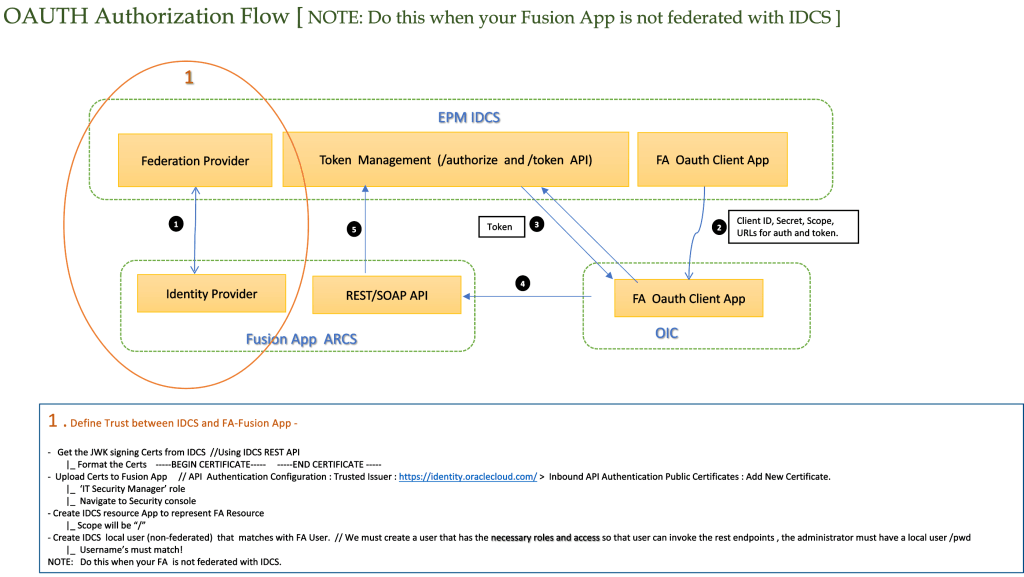
- Retrieve JWK signing certificates from your IDCS using the IDCS REST API.
- Upload the certificate to Fusion Apps under:
API Authentication Configuration → Trusted Issuer - Create a resource app in IDCS to represent the FA resource, setting the scope to “/”.
- Define a local (non-federated) user in IDCS with matching username as in Fusion Apps.
- This user must have the necessary roles and privileges to call the REST APIs.
Note: This is a one-time setup step required only when your OIC and FA are in different, non-federated IDCS or IAM domains.
2. OIC configuration

- Trust is established between the OIC IDCS and Fusion App’s Identity Provider via the uploaded certificate.
- An OAuth Client App is registered in OIC, configured with the Client ID, Secret, Scope, and URLs for
/authorizeand/token. - The OIC client app requests a token from the EPM IDCS.
- The access token is used to invoke Fusion App REST/SOAP APIs.
- Token validation is performed by EPM IDCS before granting access.
Note: The user used to complete provide consent flow is the user whose username will always go in the token when API is invoked.
Fusion App will check for username in the token
Some additional resources :
https://docs.oracle.com/en/cloud/paas/application-integration/rest-api/OAuth_prereq.html
https://docs.oracle.com/en/cloud/paas/application-integration/rest-api/OAuth_refreshtoken.html
Répondre à Securing OIC Integrations with OAuth 2.0 – Part 1: Real-World Problems, Best Practices & Practical Advice – Sanae BEKKAR – My Blog – Annuler la réponse.